Don’t Take the Bait
 Have you received strange emails asking for your credentials? Have these emails resembled methods that PNW uses? Here is some information on phishing emails and how you can protect yourself and the University.
Have you received strange emails asking for your credentials? Have these emails resembled methods that PNW uses? Here is some information on phishing emails and how you can protect yourself and the University.
What are phishing emails?
Phishing emails are a type of social engineering attack that are used to obtain information about a person or organization. A malicious actor will try to take you to malicious sites that can capture your login information. They might even send you attachments that contain malware! The data obtained can be used to infiltrate an account or an organization’s network.
What do they look like?
Attackers will try to mimic an organization logo or email template. This is done to encourage you to click on links or open malicious attachments.
It is common for phishing campaigns to take advantage of current events and times of the year. For example, you can see an increase during:
- Start of a new semester
- Natural disasters or epidemics
- Tax season
- Political elections
- Holidays
Examples from phishing.org:

The email above was delivered through LinkedIn, as did the URLs used for the several links included in the footer of this email (“Reply,” “Not interested,” “View Wells’s LinkedIn profile”). Those URLs were obviously auto-generated by LinkedIn itself when the malicious actors used LinkedIn’s messaging features to generate this phish, which hit the external email account of the user. There are also grammatical errors throughout the email.
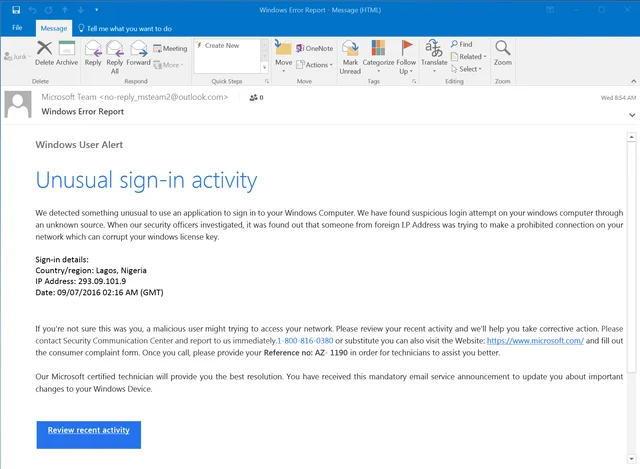
Here’s a fake Microsoft notice, almost identical in appearance to an actual notice from Microsoft concerning “Unusual sign-in activity”. This email points users to a phony 1-800 number instead of kicking users to a credentials phish. There are also grammatical errors throughout the email.
How can you avoid being a victim?
- Pay attention to links and where they are taking you. The URL may have misspellings or a different domain (e.g., .com vs .net). You can use the following websites to scan a web address to get more insight into how the link behaves and help determine if it is malicious. Right-click the hyperlink and choose copy address, then paste the web address on their website and their services will scan, analyze, and report their findings.
- If you get a suspicious link that wants you to log in, go to the vendor’s website on your own instead to view any alerts and activity. Going to the official website on your own can bypass any potentially malicious content.
- Always verify the sender is legitimate.
- Don’t send sensitive data through email. You can refer to the Purdue Data Classification and Handling information.
- You can report any suspicious communications to abuse@pnw.edu. If it is a personal account, you can email a third party to report the malicious communications.